Basic principles of identification protocols – Entity Authentication
5.1.1 Basic principles of identification protocols
The simple exchange of a question and an answer between Alice and Bob described previously can be seen as a rudimentary identification protocol. We touched on this subject in Section 2.5, Authentication in Chapter 2, Secure Channel and the CIA Triad, and will now provide some more details.
But before diving into the details, we first need to introduce some basic definitions used in the context of identity and identity verification in cryptography.
In cryptography, the communicating party who assures themselves of the identity of the other communicating party is called the verifier. The communicating party claiming a specific identity is called the claimant. The claimant performs some calculations that only they can perform (we’ll see later how that works) and the verifier validates that these calculations are correct and that the identity declared by the claimant is their actual identity. This prevents the threat of impersonation, the act of assuming someone else’s identity.
Recall from the Section 2.5, Authentication in Chapter 2, Secure Channel and the CIA Triad that a cryptographic protocol is a distributed algorithm specifying the action required of two or more entities to achieve a specific security objective [117]. Because in entity authentication, we are interested in verifying who we are interacting with, a cryptographic protocol is a suitable framework for this task.
Figure 5.1 shows the working principle of a typical cryptographic protocol for identity verification. The verifier requests the claimant to send her a message, let’s call it m, which demonstrates that the claimant is in possession of some secret that only the genuine party can know by design. In response, the claimant computes and sends message m to the verifier. Upon receiving m, the verifier checks the correctness of the message and accepts the claimant’s identity if the check is successful. Such cryptographic protocols are referred to as identification protocols or entity authentication protocols. When analyzing the security of such protocols, we need to bear in mind that in most cases the channel that is used to exchange the protocol messages is insecure. In particular, this means that even after the identity check, an attacker might still take over the channel. This problem can only be resolved by combining entity authentication with authenticated key establishment, which we will discuss in the next section.
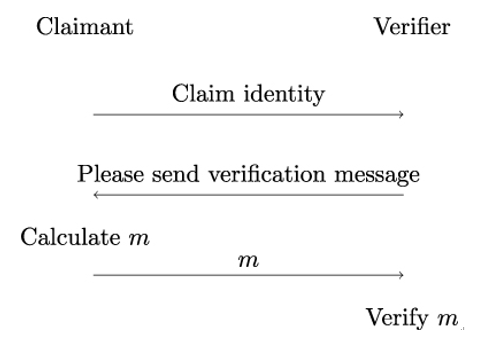
Figure 5.1: Working principle of entity authentication protocols
Figure 5.1 shows a situation where only the claimant authenticates against the verifier. This is called a uni-lateral authentication. Oftentimes, the verifier and claimant switch roles after the claimant has authenticated so that the other party also authenticates. This process is called mutual authentication.

