Challenge-response protocols – Entity Authentication
5.5 Challenge-response protocols
The working principle of cryptographic challenge-response protocols is illustrated in Figure 5.5. Claimant Bob proves his identity to verifier Alice by demonstrating that he knows a secret that, by design, is known only to Bob (and, potentially, Alice). However, unlike with basic password-based authentication, as shown in Figure 5.3, Bob does not reveal the secret on the communication channel.
Instead, Bob responds to a time-variant challenge. Computing the correct response requires both Bob’s secret and the challenge. The challenge, for example, a number, is chosen by verifier Alice randomly and secretly at the beginning of the protocol.
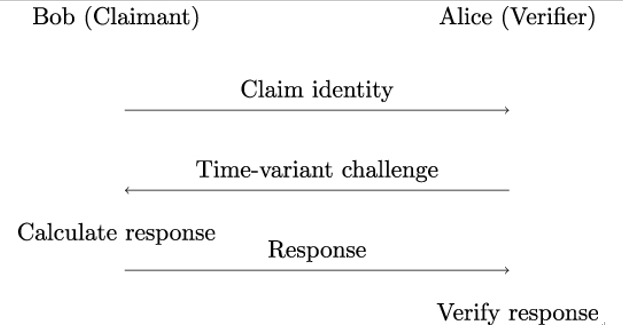
Figure 5.5: Working principle of entity authentication protocols
Why are challenge-response protocols more secure than passwords, and how do they overcome the drawbacks of password-based authentication we discussed previously?
First, the claimant never discloses the secret. Unlike with passwords, the secret used in a challenge-response protocol never leaves the claimant’s machine (or whatever form of storage the claimant uses to store their secret). What is transmitted from the claimant to the verifier is a response generated using the claimant’s secret.
Because the claimant’s secret is typically a cryptographic key that has sufficient entropy, and the response is obtained by encrypting (or decrypting) the challenge with that key, or by computing a key-dependent hash value of the challenge, recovering the claimant’s secret from the response would require the attacker to break the encryption or hashing algorithm. Luckily, this is practically infeasible for modern encryption algorithms such as AES.
Second, a challenge-response protocol always employs a time-variant challenge generated by the verifier. Most importantly, this means that the challenges will not repeat. A repeating or constant challenge would mean that the response also stays the same, and an active attacker, Mallory, could impersonate Bob simply by replaying a previously eavesdropped response. A time-variant challenge, on the other hand, means the response has a new value for each protocol run. As a result, even if Eve manages to read all communication between Alice and Bob, the response from one execution of a challenge-response protocol does not provide her with any information she could use to impersonate the claimant Bob in future protocol executions.

