Message authentication versus entity authentication – Entity Authentication
5.3 Message authentication versus entity authentication
What happens if message authentication or entity authentication fails? We can answer this question by looking at Figure 5.2 again. There are two ways in which Eve can manipulate messages sent from Bob to Alice. Eve’s first option, illustrated on the left-hand side in Figure 5.2, is to break the message authentication of the communication between Alice and Bob by suppressing the original messages, changing them, or replacing them with messages of her own. Eve’s other option, shown on the right-hand side in Figure 5.2, is simply to replace Bob in the communication and receive Alice’s messages instead of Bob, or send Alice any message of Eve’s choice, thereby breaking entity authentication.
The difference between entity authentication and message authentication is further illustrated by the notorious email-based phishing attacks you are all familiar with. In this case, an attacker sends you an email allegedly coming from your bank, telling you there is a problem with your online banking account and that you have to log in within the next 24 hours, otherwise your account will be canceled. Helpfully, there is also a link provided in the email for you to log in. If you click on that link, the attacker has achieved their first goal: you believe the email really comes from your bank, which is a violation of message authentication.
Clicking on the link will bring you to some web server controlled by the attacker. It certainly claims to be the banking server, it may even look like the banking server, but it isn’t the banking server. If you fail to notice this, entity authentication is broken, and you provide your login credentials to some fake server. Luckily, TLS provides us with the means to verify whether we are really connected to our banking server or not.
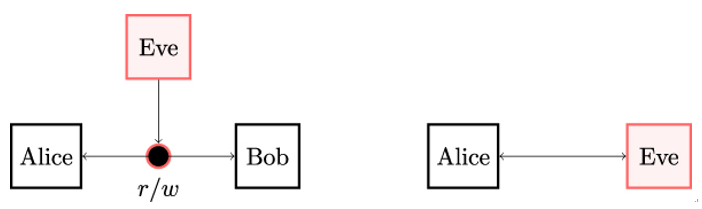
Figure 5.2: Eve can succeed either by attacking the communication channel or by impersonating Bob
Another fundamental difference between message authentication and entity authentication is the fact that message authentication does not guarantee timeliness. Using message authentication, Alice can be assured that Bob is indeed the source of a message m she received and that the message was not altered during transmission. However, Alice has no way to tell whether Bob sent the message m a minute or a year ago.
Entity authentication, on the other hand, involves validating the claimant’s identity in real time through dedicated communication between the claimant and the verifier [117]. If Alice and Bob execute an entity authentication protocol before exchanging messages, Alice knows that Bob is actually online and, as a result, that the messages she receives from Bob are fresh. This, in turn, protects Alice against so-called replay attacks, where Eve replays Bob’s messages that she recorded in the past.

