Session resumption – Transport Layer Security at a Glance
6.5.3 Session resumption
Establishing the value of the PreMasterSecret is computationally the most expensive part of the handshake because it involves public-key cryptography. TLS therefore includes a session resumption mechanism, where a client and server can reuse an already established session, including the cipher suite and the MasterSecret derived from PreMasterSecret. The client initiates the process by including the session ID of the previous session in its ClientHello message. If the server agrees to the resumption, it includes the same SessionID in its ClientHello message. There is no need to negotiate algorithms or keys. Figure 6.6 shows the reduced handshake in this case. Note that reusing MasterSecret does not mean that the keys used for protecting the application data in a connection are the same as before. That’s because these keys are derived from MasterSecret using the random numbers that are included in the ClientHello and ServerHello messages. These numbers are different for each connection, even when a session is resumed.
6.6 TLS version 1.3
In the years since its inception, TLS and its predecessor, SSL, have suffered a lot of attacks, both at the protocol level and the algorithm level (we will be discussing a few of them in Part IV, Bleeding Hearts and Biting Poodles). Step by step, these attacks have been mitigated in new TLS versions and extensions up to version 1.2. However, due to the need for backward compatibility and the resulting possibility for version rollback attacks, each new TLS version inherited the weaknesses of its predecessors. For example, the cumulative number of cipher suites in all TLS versions up to version 1.2 is 319, including a large number of outdated and insecure algorithms.
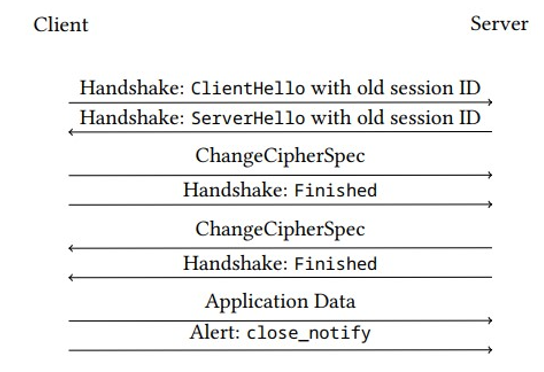
Figure 6.6: Overview of TLS session resumption (up to V1.2, adapted from [146])
Therefore, in 2018, it was time for a larger clean-up: unsafe or unused options were removed in version 1.3, and version downgrade attempts are signaled to the client by the last eight bytes of Server˙Random. Moreover, SSL version 3.0 has been generally deprecated.
While the basic subprotocol structure with a handshake protocol and a record protocol was retained in TLS version 1.3, some major changes were made within the handshake protocol. We will now take a detailed look at this new handshake and discuss the changes in comparison to version 1.2 in Section 6.7, Major differences between TLS 1.3 and TLS 1.2.

