Zero round-trip time mode – Transport Layer Security at a Glance
6.6.4 Zero round-trip time mode
If two TLS endpoints share a secret key, TLS 1.3 allows them to communicate over a secure channel right from the start. This is referred to as 0-RTT, a zero round-trip time mode added in TLS 1.3 to save one round trip for the application data during the initial handshake, albeit with a decreased level of security. In other words, 0-RTT is a feature that allows TLS 1.3 to reduce the protocol latency by allowing client Bob to send data to server Alice in the first round-trip, without waiting for the Alice’s response.
Figure 6.11 illustrates the 0-RTT mode. The client uses the shared key to authenticate the server and to establish a secure channel for the early data. The early data is simply added to the standard 1-RTT handshake. The remaining handshake is the same as the 1-RTT handshake with session resumption.
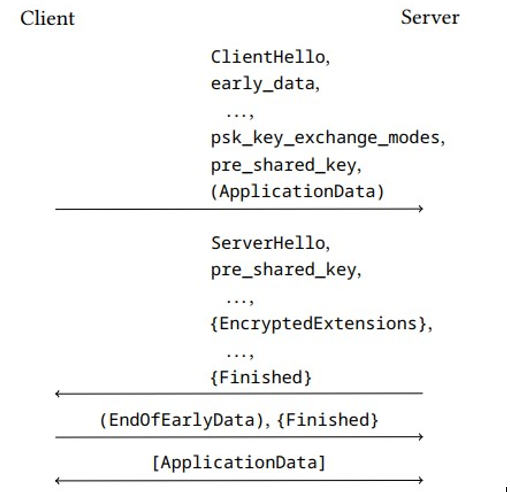
Figure 6.11: Message flow in a 0-RTT handshake introduced in TLS 1.3
However, 0-RTT data is less protected. First, forward secrecy does not hold for this data because it is encrypted using keys derived from the PSK rather than fresh, randomly generated key shares.
Second, 0-RTT data is not protected against replay attacks. Regular TLS data is protected against this type of attack by the server’s random variable. 0-RTT data, in contrast, does not depend on the ServerHello message and therefore lacks fresh randomness from the server.
6.7 Major differences between TLS versions 1.3 and 1.2
While the focus of this book is to gain an in-depth understanding of the cryptography used in TLS 1.3, it is instructive to look at the changes TLS designers made between version 1.2 and version 1.3.
Insecure or unused cryptographic algorithms such as RSA, RC4, and SHA-1 and insecure modes of operation such as the Cipher Block Chaining (CBC) mode were either removed completely or, as in the case of SHA-1, only retained as legacy algorithms to ensure the verifiability of older certificates.
Further cryptographic improvements include the removal of compression, the Digital Signature Algorithm (DSA) (see Chapter 9, Digital Signatures), and client-generated ephemeral Diffie-Hellman groups.
A famous phrase in cryptography is that attacks only get better over time. Consequently, cryptographic algorithms and primitives do become insecure eventually and need to be exchanged. As a result, there are only five remaining cipher suites in TLS 1.3:
- TLS˙AES˙128˙GCM˙SHA25
- TLS˙AES˙256˙GCM˙SHA384
- TLS˙CHACHA20˙POLY1305˙SHA256
- TLS˙AES˙128˙CCM˙SHA256
- TLS˙AES˙128˙CCM˙8˙SHA256
Maybe you have noticed that public-key-based algorithms for key agreement are missing in these cipher suites. For comparison, look at this fairly common TLS 1.2 cipher suite:
- TLS˙ECDHE˙RSA˙WITH˙AES˙128˙GCM˙SHA256

